CISSP는 아는데 CBK를 모르세요?
 최근에 정보(시스템) 보안에 관해서 신문 지상을 장식하는 주제들이 많이 등장하고 있다. 최근의 DDOS(Distributed Denial of Service: 분산서비스공격)는 물론 계속 이슈가 될 것인 PIA(Private Impact Assessment: 개인정보 영향평가) 등등, 누군가의 말처럼 컴퓨터를 켜지 않는 것만이 정보보안의 최선책이라는 말이 나올 정도이다.
최근에 정보(시스템) 보안에 관해서 신문 지상을 장식하는 주제들이 많이 등장하고 있다. 최근의 DDOS(Distributed Denial of Service: 분산서비스공격)는 물론 계속 이슈가 될 것인 PIA(Private Impact Assessment: 개인정보 영향평가) 등등, 누군가의 말처럼 컴퓨터를 켜지 않는 것만이 정보보안의 최선책이라는 말이 나올 정도이다.
이렇게 정보보안이 사회적인 문제가 될 때일수록, 알고서 대응하는 현명한 자세가 필요하며 (ISC)2에서 오랜 기간 정보보안 체계를 만들어 온 CBK(Common Body of Knowledge: (정보보안)지식체계)를 이해하는 시간을 갖도록 하겠다. CISSP (Certified Information System Security Professional: 국제공인 정보시스템 보안 전문가) 자격증을 소지하고 있는 정보보안 전문가이면 누구나 한번 이상은 공부하는 CBK에는 정보보안에 대한 성경이라고 할만큼의 방대한 지식과 실무가 있다. 작금의 정보(시스템) 보안에 대한 필요성이 더욱 절실할 때 기본으로 돌아가서 CBK와 함께 난세를 헤쳐나가 보도록 하겠다.
<게재 순서>
①CBK의 개요
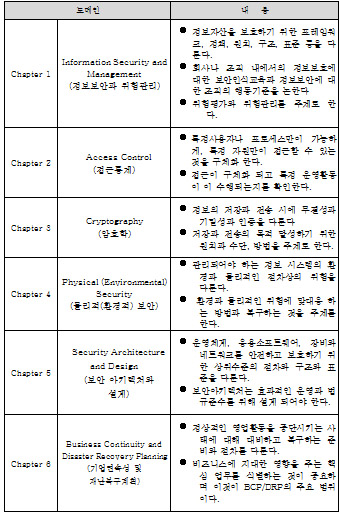
②Domain 1 Information Security and Management(정보보안과 위험관리)
③Domain 2 Access Control (접근통제)
④Domain 3 Cryptography (암호학)
⑤Domain 4 Physical (Environmental) Security (물리적(환경적) 보안)
⑥Domain 5 Security Architecture and Design (보안 아키텍처와 설계)
⑦Domain 6 Business Continuity and Disaster Recovery Planning (기업연속 및 재난복구계획)
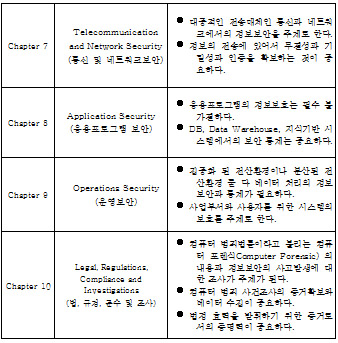
⑧Domain 7 Telecommunications and Network Security (통신 및 네트워크 보안)
⑨Domain 8 Application Security (응용프로그램 보안)
⑩Domain 9 Operations Security (운영보안)
⑪Domain 10 Legal, Regulations, Compliance and Investigations (법, 규정, 준수 및 조사)
CBK의 개요
CBK(Common Body of Knowledge: (정보보안)지식체계) 라고 하면 단어에서 얘기하는 대로 지식체계이다. 정보 및 정보시스템 보안(보호)에 대한 지식 체계이다. 필자가 CBK를 대하면서 느끼는 것은 지식체계와 실무를 겸비해 놓았다는 것을 확신 할 수 있다. 원고가 연재되는 순서를 보면 주제별로 정리해 놓았다. 주제별이라고 한다면 보안이나 보호해야 할 대상, 즉 정보(Information)와 그 정보에 영향을 끼치는 것들을 모아 놓았다고 보면 된다.
정보라고 하는 것이 보호의 대상이 될 수 있는 모든 매체(media)를 도메인(domain)화 하여 소개하고 있다. 무려 10가지나 된다. 또한 주제별로 저자가 다 다르다는 것을 알 수 있다. 전문성과 실무를 최대한으로 끌어 올리기 위해서 그렇게 집필 했다고 할 수 있다. 그래서 CISSP (Certified Information System Security Professional: 국제공인 정보시스템 보안 전문가)를 위한 분류학(taxonomy) 이라고 불리기도 한다.
더욱이 놀랍기도 하고 엄두도 안 나는 것이 CBK 책자의 분량이다. 무려 1,100여 페이지에 다다른다. 가지고 다니면서 틈틈이 보기 위해서는 부득이 분철을 해야 할 정도의 분량이다. 아직은 한글화가 안되었다는 것이 또한 아쉽지만 CISSP Korea (ISC2의 한국 chapter)의 역할과 활약이 중요시 되고 또한 협회의 전문가들의 능동적 활동으로 향후를 기대해 보기로 한다.
지식체계를 이해하기 위해선 지식체계와 자격증을 만들어 낸 (ISC)2에 대해서도 알아볼 필요가 있다. 정보보안(보호에) 대한 필요성을 느낀 국제 조직들이 1989년에 컨소시엄을 형성하여 설립한 것이 (ISC)2 (International Information Systems Security Certification Consortium)이다. 두문문자(acronym)로 IISSCC로 표기하기 보다는 수학공식을 적용해서 (ISC)2로 표현하는 센스도 엿 보인다.
앞으로 다루게 될 주제영역별 도메인을 살펴보도록 하겠다.
간략하게 살펴본 내용으로 보아서 정보(Information)라고 하는 것은 기업이나 조직, 심지어 개인에게 까지 중요한 자산이다. 중요한 자산인 정보는 CBK의 내용처럼 너무나 여러 가지 형태로 존재하고 있고, 또한 가만히 있지 않고 정보라는 특성이기에 누군가와 주고 받아야만 한다. 금고 속에 가만히 꽉 잠 구어 놓을 수만 있다면 그나마 소중한 정보를 보호하는 방법이 될 텐데, 정보는 흘러가지 않으면 아무 의미가 없다는 것은 독자들이 잘 알 것이다.
정보의 속성상 주고 받아야 하고 계속 진화해야 하는 그 특성 때문에 정보는 가치가 있고, 그러기에 보호나 보안 또한 쉽지는 않다. 전문적인 정보보호, 정보보안 전문가에 의해서 다루어 질 수 밖에 없다. CISSP (Certified Information System Security Professional: 국제공인 정보시스템 보안 전문가) 의 역할과 책임이 꼭 필요한 시대의 요구를 시사하고 있다고 하겠다.
지금은 농경사회도 아니, 상업사회도 아닌, 지식사회이다. 정보를 가진 자가 힘이 있는 자이다. 그러기에 정보를 보안하고 정보는 보호해야 하는 것이다. CBK의 도메인 별 내용을 연재로서 실어 봄으로서 지식사회의 지식인이 되어보는 지식활동에 도움이 되길 바란다.
보다 자세한 내용은 http://www.isc2.org/혹은 http://www.cisspkorea.or.kr/에서 찾아볼 수 있다.
참고자료 및 출처
www.isc2.org
www.cisspkorea.or.kr
Official (ISC)2 Guide to the CISSP CBK, Auerbach Publications, 2007~2008
Information Security Governance, ITGI, 2008
InfoSecurity Professional Magazine, ISC2, 2008~2009
[필자 약력]
-기고자: 조 희 준
-IT컨설팅 및 감리법인 (주)키삭 책임컨설턴트 재직 중
-고려대학교 대학원 감사 행정학과 재학 중
-(사)한국정보시스템 감사통제협회 ISACA GRA 연구회원
-한국 CISSP 협회 ISC2 Korea 교육연구분과 교육팀장
-CISM, CGEIT, CISA, COBIT, CISSP, PMP, ITIL, CIA, IT-EAP, ISO 27001 정보시스템 감리원
글·조희준(CISM, CGEIT, CISA, COBIT, CISSP, PMP, ISO27001, CIA, 정보시스템감리원) / josephc@chol.com
[정리 길민권 기자(reporter21@boannews.com)]
<저작권자: 보안뉴스(http://www.boannews.com/) 무단전재-재배포금지>

.jpg)

.jpg)
.png)








 길민권기자 기사보기
길민권기자 기사보기






























.gif)






.png)
.jpg)











